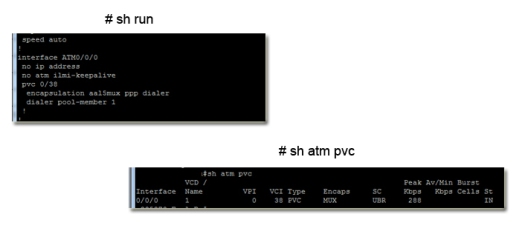
Below shows 2 categories in which devices fall into, when connecting over a dsl connection. Either a 800 series router can be used or a DSL WIC card will be used by connection it in another series Cisco router. Note:- There will be other methods of connecting, however my focus is only on these two methods here.
* BT UK ADSL2+ Annex-A using Cisco STM Products [857,867,877,887, HWIC-1-ADSL*] – HWIC ADSL modules are based on the ST Micro 20196-PA chipset
* BT UK ADSL2+ Annex-A using Cisco BRCM Products [887-VA and EHWIC-VA-DSL-A] – EHWICs support multimode ADSL2/ADSL2+/VDSL technologies based on the Broadcom chipset. The Cisco 880VA Series Multimode VDSL2/ADSL2+ platforms are based on the same Broadcom chipset and support the same DSL modem firmware.
Since IOS 12.4(3)T, ADSL firmware has been separated into an additional.bin microcode update. The IOS versions do have embedded firmware, however the standalone firmware is preferred for almost all connections.
For 857,867,877,887, HWIC-1-ADSL* (which use ST Micro 20196-PA chipset):
To upgrade the firmware a dsl firmware file needs to be downloaded and renamed as “adsl_alc_20190.bin”. It can then be uploaded to flash (TFTP/SCP shown later in post.)
- Download Firmware from – http://software.cisco.com/download/navigator.html Branch routers>800 Series>(pick a router from the above list i.e. 857)>ADSL Firmware
- Copy Firmware to Flash and ensure the name is “adsl_alc_20190.bin
- Reboot the device for firmware to take effect.
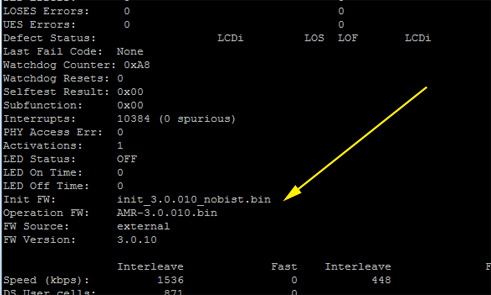
- “#show dsl interface atm 0” – Should show the firmware source as external rather then embedded!
The two main fields to be concerned with here are FW Source and FW version (The naming convention of the firmware is also displayed above these).We can verify the firmware has been applied as the FW Source = external
If this read embedded it would still be using the embedded firmware, and there was an error in it using the installed firmware (one thing to check in this scenario is ensuring the file is named adsl_alc_20190.bin)
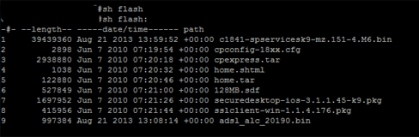
The below image shows the outcome of a show flash command:
Here you can verify the naming convention of the file, also notice that although the #show dsl interface atm 0 or 0/0/0 shows the firmware name as different to the file name, (((Investigate issue))))
For 887-VA and EHWIC-VA-DSL-A (supporting multimode ADSL2/ADSL2+/VDSL technologies based on the Broadcom chipset):
- Download firmware from – http://software.cisco.com/download/navigator.html Branch routers>800 Series> (select the router i.e Cisco 887VA Integrated Services Router) > Select Very High Bitrate DSL (VDSL) Firmware
- Copy the firmware to flash
- Configure the router to load from specified location (done under vdsl controller interface) Router(config)#controller vdsl 0
Router(config-controller)#firmware filename flash:vdsl.bin.bdslfw
Router(config-controller)#modem UKfeature under controller vdsl 0 (may not tab and must be typed in exact) - Restart controller by shut/no shutting the controller
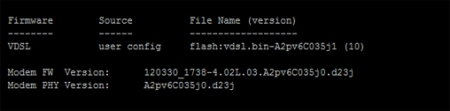
- Verify by – Router#show controller vdsl 0
As you can see here the source is user config, this show it is using the firmware we sent to the routers flash and reference under the controller in running config. a show flash command will verify the file name. Also bear in mind, that when using this process, the vdsl controller can be rebooted rather then the entire device.
Useful Links:
During the process of check compatibility with WICs and BT DSLAMs the following sites were ones i found useful and used for reference:
- https://www.cisco.com/en/US/prod/collateral/routers/ps10536/qa_c67-644632.pdf — Tells you a little bit more about the EHWIC VA DSL card, and also touches on a few differences between the EHWIC VA and the HWIC-1-ADSL card.
- http://www.cisco.com/en/US/prod/collateral/routers/ps380/qa_c67-612339.html — Tells you more about the 880-VA series routers and talks a little about the models i.e 887VA-A (annex A), 887-va-m (annex M) and so on.
- http://www.cisco.com/en/US/prod/collateral/routers/ps380/qa_c67-532551_ps380_Products_Q_and_A_Item.html — Useful for checkin incompatibility between routers/WICs and specific DSLAMs
- http://software.cisco.com/download/release.html?mdfid=283122091&flowid=20441&softwareid=282821780&release=A2pv6C038k1&relind=AVAILABLE&rellifecycle=&reltype=latest# — link to the latest 887VA firmware, but from this page you can also navigate around for other available software.
- http://stewartandrews.wordpress.com/2012/06/28/cisco-cpe-and-compatibility-with-bt-adsl-services/ — Quite similar to the above information, but looks to go into more detail. Some useful stuff here.