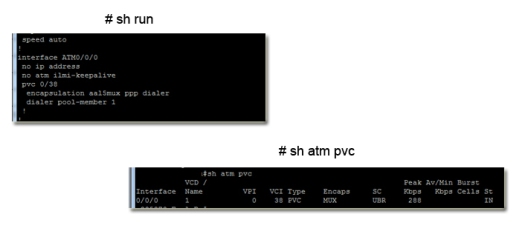
The following article talks you through the basic set up of an IPSEC connection on a cisco, with debugs along the way. It also shows you the set up between a cisco and a speedtouch.
Set up of a Cisco IPSEC
Below show the set stages i go through when creating an IPSEC.
1. Create the Policy (Phase 1)
Each tunnel is created under a policy, if there are multiple tunnels i tend to create a seperate policy for each . When creating phase 1 i always use the term HAGLE to remember what is needed (thanks to CBT).
Router(config)# crypto isakmp policy 1
Router(config-isakmp)# Hash MD5
Router(config-isakmp)# Authentication Preshare
Router(config-isakmp)# Group 2
Router(config-isakmp)# Lifetime 3600
Router(config-isakmp)# Encryption 3DES
As we are using a pre-shared key we also must set the pre-shared key(in plain text), for phase 1 this is done by entering the command below and applying it to the remote peer address.
Router(config)#crypto isakmp key 0 TRANSFORM address 20.0.0.1
This will successfully create the attributes needed for the phase 1.
2. We can then start the Phase 2.
This is initially started by creating a transform set and applying the phase 2 attributes to this, e.g md5, 3des etc…To do this we start with the following command.
Router(config)#crypto ipsec transform-set TRANSFORM esp-3des esp-md5-hmac
Router(cfg-crypto-trans)# end
Note:- there are more options in (cfg-crypto-trans)# mode, i.e transport/tunnel mode encapsulation, but for this example we can just end the config and move onto the next stage.
To complete Phase 2 we need to create a cryptomap, that will link to the transform set, this crypto map allows us to add finer details to phase 2 using the ‘set’ command. We also need to used the ‘match’ command to link it to the interesting traffic that will need to be crypted to pass through this tunnel.
Router(config)#crypto map OUTMAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Router(config-crypto-map)#set peer 20.0.0.1
Router(config-crypto-map)#set transform-set TRANSFORM
Router(config-crypto-map)#match address 101
The above is a basic set up, but if the lifetime (re-key interval) needs to be set for phase 2 we do this the following way.
Router(config-crypto-map)#set security-association lifetime ?
kilobytes Volume-based key duration
seconds Time-based key duration
The final set here is to apply the crypto maps to the correct interfaces (the exit interfaces for the two tunnels)
Router(config)#int fa 0/0
Router(config-if)#crypto map OUTMAP
3. Match the Interesting traffic
An access list needs to be created for the interesting traffic, this is basically telling the router – any traffic matching this acl needs to pass through this tunnel. An example ACL is below:
Router(config)#ip access-list extended 101
Router(config-ext-nacl)#permit ip 172.16.0.0 0.0.0.255 172.16.50.0 0.0.0.255
IMPORTANT NOTE: – Remember this acl does not do any routing, it is just an identifier as to what traffic is allowed. When traffic hits the router it needs to look at the routing table first then be read by and acl (this is an exception for acls assigned to an interface preventing traffic inwards).
With the above in mind – There needs to be a route for the Interesting traffic, this can either be a specific route or a default route, so that a packet knows what interface to go out.
4. NAT – ing (additional step)
The above 3 steps are all thats needed for the configuration, however there will be times when you are setting up a tunnel and the local traffic will need to access the internet. If this is the case we need to NAT the traffic, but we need to ensure the IPSEC traffic is not NATed to do this we will need the following configuration.
4.1 Create NAT pool:
ip nat pool CUST-NATPOOL 10.10.10.0 10.10.10.10.7 netmask 255.255.255.248
ip nat inside source route-map NONAT pool CUST-NATPOOL overload
4.2 Create Routemap for NAT pool:
route-map NONAT permit 10
match ip address 110 <<<<<<<< This is the acl for the nat pool.
4.3 Create ACL for NAT Pool, (what traffic gets Nat-ed and what doesn’t):
ip access-list extended 110
deny ip 172.16.0.0 0.0.0.255 172.16.50.0 0.0.0.255 <<<<<< 0.0 to 50.0 deny from being Nat-ed
permit ip 172.16.0.0 0.0.0.255 any <<<< everything else can be Nat-ed
(Obviously the more ipsec’s the more statements will be needed)
4.4 Apply IP NAT inside/Outside to relevant interfaces:
Fa0/0 – IP NAT OUTSIDE
Fa0/1 – IP NAT INSIDE
And that’s it, this should be more then enough to get the tunnel working, remember the tunnel will only come up when interesting traffic is generated. So Pings need to be sourced from the relevant interfaces.
Both ends of the IPSEC tunnel have to match, so a mirror config of the above, will get a tunnel between two Cisco’s working. I however used the above config to work alongside a Thomson (covered later). The next section shows the show commands i used to verify connectivity.
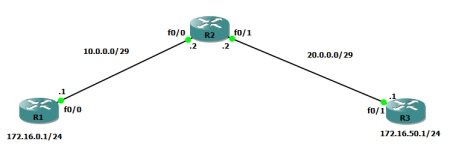
Here is a topology diagram which shows a basis for what we just set up:
Show Commands for Cisco IPSEC
The main show command is to check to see Phase 1 is up, this can be done by the command:
Router# sh crypto isakmp sa
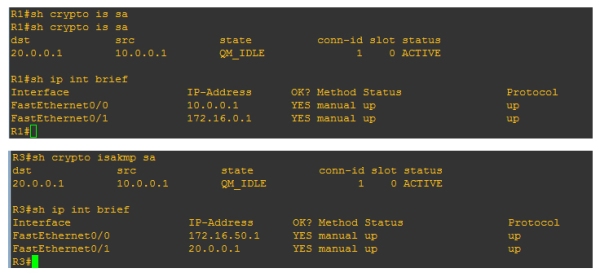
Above is the same command on both routers, here we would expect to see different source and destinations, but they are both the same! This is because the source is always going to be the IP that initiated the tunnel (brought the tunnel up). So for example: on R3 router the source for the isakmp is 10.0.0.1, even though the interface for that router is 20.0.0.1 this is because the the tunnel was brought up by the R1 router, so the source will always be the R1 router. If the tunnel was brought up by R3 then the source and destination will be the other way round on both routers.
Note: – Also worth noting the states QM_IDLE and status ACTIVE are good. This is basically meaning that the ISAKMP SA is authenticated and can be used for subsequent Quick Mode (Phase 2) exchanges. When you delete a state you will see MM_NO_STATE and ACTIVE (deleted) – You may still be able to ping across the tunnel even if this is the state. This is because we would need to wait till Phase 2 goes down (either via no traffic or DPD notification).
Phase 1’s duty was to bring the table up, and as that was done successfully bringing the tunnel down may not always stop connectivity.
Another show command used to verify is
Router#sh crypto map
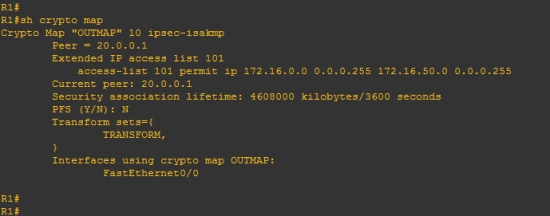
This allows us to see a lot of information about how everything is linked when traffic goes over the tunnel (i.e what map is used, what acl is used, what interface it goes out from etc…) It is also useful as it will tell us if something is missing. The above crypto map is fine, so we see no message but if there is an issue we may see a message like this: WARNING: This crypto map is in an incomplete state! (missing peer or access-list definitions)
Router#sh crypto isakmp policy
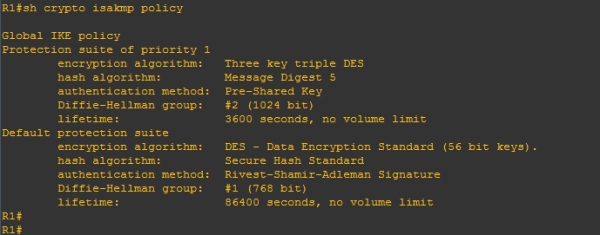
Shows details specifically about the phase 1, this is useful when phase 1 is not coming up and you need to match the attributes against both sides.
Other commands which are useful:
show crypto ipsec sa – Details and informaion about phase 2.
show run and show run all – The show run all command shows all the default settings which are not really shown in a simple show run.
You must remember to verify ACLs are OK and also that static routes are set up if needed.
Creating the Tunnel on a Speedtouch/Thomson
As promised, I will show you how the tunnel was created on the Thomson, this tunnel has to be created in expert mode of the device once logged into the GUI.
1. Create the tunnel.
So once in expert mode navigate to VPN>LAN to LAN. On this page you can start entering the details for the phase one. The descriptors are viewed on a different page, this will show you what encryption etc… is being used. However best practice is to just take note of the descriptors and come back to it once completed Phase 1 and Phase 2. Once we have entered details for the Phase 1 (see below), we can start save/apply and then click New connection to this gateway(to start phase 2 details)
Note:- The images will use the same IP address scheme as the R3 router in the above cisco scenario (this is so it is easier to follow).
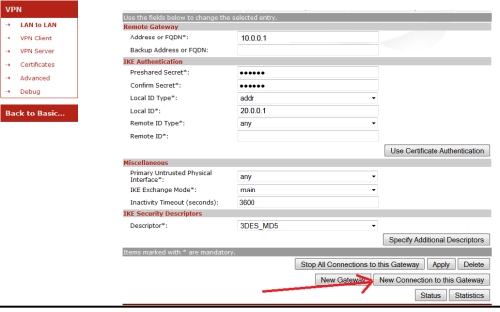
Once phase 1 is added, and you have clicked new connection to this gateway, you can start filling in details for Phase 2. Fill in the needed details using / notation for the local and remote lan ranges and ensure to select a descriptor (note down the name so it can be verified – shown on next step).
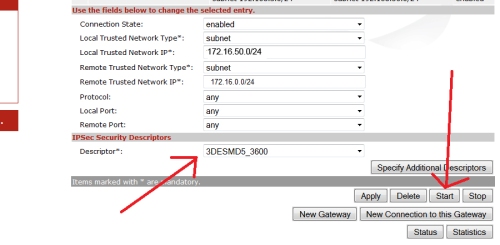
If you navigate to VPN>Advanced. You can see the desciptors used for both Phase1 and Phase2
Phase 1 is under Peers> Descriptors
Phase 2 is under Connections > Descriptors (the below image shows phase 2 descriptors).
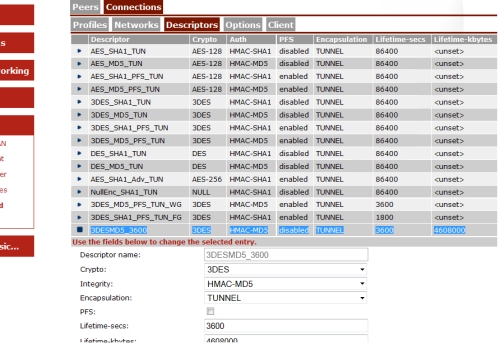
You can verify what settings the device is using by comparing it to the descriptor selected under the phase1/phase2 settings. So for example, on phase 2 we have 3DESMD53600 selected as a descriptor. This tells us that phase2 is using 3des,md5, pfs = disabled,lifetime 3600 etc…
The pre-set templates can be used, or you can create your own custom ones.
2. Configure the Routing
Remember there needs to be a route in place so the traffic knows where to go, on the speedtouch the route has to be more specific and is done from the CLI.
Telnet into the routers cli and add the following command:
ip rtadd dst 172.16.1.0/24 intf=ipsec0 srcintf=LocalNetwork
ip ipconfig addr=172.16.50.1 primary=enabled <<<<<<<< this is routers local IP
Note: – If ICMP does not work you have to ensure the responder is enabled on each interface, go to speedtouch > speedtouch services > icmp eco responder, and then select the interfaces you want icmp to respond on, I.e tunnel and wan and lan etc…
This was the basic process i went through to set up the IPSEC. I did come across some problems, however if you follow the above you should be fine. The next section does details some of the issues i came across.
Problems I came across
When configuring this there were a few problems i came across, some are quite simple however i have detailed them below:
Phase 1 would not come up when initiating traffic from the Cisco, but was fine when bringing the tunnel up from the speedtouch. For diagnosing this i used the speedtouch debug information, and initiated a ping from the cisco.
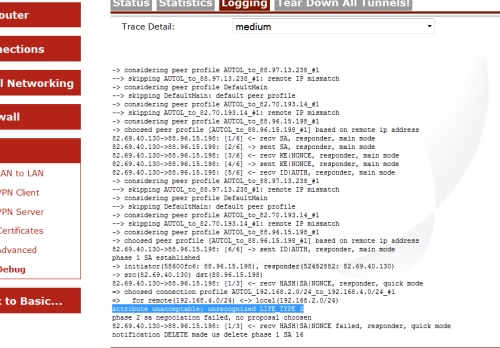
From the debug, i have picked out one specific line ‘attribute unacceptable: unrecognized LIFE_TYPE 2’ – at first i didnt know what this meant but through a lot of testing it is basically telling the following-
The Cisco is sending 2 phase 2 life-types to the Thomson, one for seconds and one for kilobytes. Normally phase 2 will just work with the lifetime in seconds attribute, but for some reason when creating a tunnel between a Cisco and a Thomson both need to be set. In the Thomson i navigated to the descriptors for Phase 2 and created a new descriptor with the kilobytes set exactly the same as the Cisco and use this for the tunnel.
To verify the lifetimes used in the Cisco (as i didnt set they would be using defaults, if they were set they would show in the running config under the crypto map) i did the following:
Router#sh crypto ipsec security-association lifetime
Security association lifetime: 4608000 kilobytes/3600 seconds
After making sure both matched, i sourced a ping from the Cisco and the tunnel came up!
Note: – I did try disabling the kilobyte life-type in the Cisco, however this still did not work for me, so it was easier to just set the attribute in the Thomson.
Another issue i came across was that ICMP was not working over the tunnel, yet the ICMP traffic was clearly hitting the tunnel and brining it up (i could see this in the debugs).
This was a simple fix, yet it was quite confusing. The fix was that there was no route in the speedtouches routing table to the remote connection at the other end of the IPSEC.
I entered the following command in the speedtouch/Thomson CLI and a route for the tunnel was added.
ip rtadd dst 192.168.50.0/24 intf=ipsec0 srcintf=LocalNetwork
ip ipconfig addr=192.168.3.254 primary=enabled
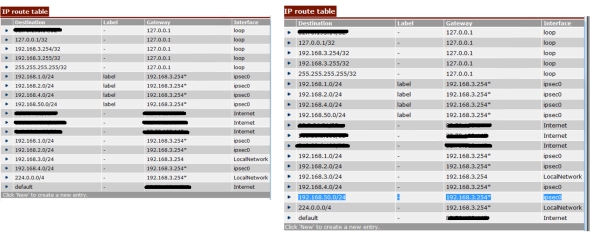
Below shows a before and after screen shot of the IP routing table. As you can see on the before screen shot there is already a route to network 192.168.50.0, but this has a label called label?? im not 100% why this is not enough for the routing table, but after adding that command a new route appears for the 192.168.50.0 network. With this in the table we are able to ping across the tunnel.
This post is a basic overview of what i went through when trying to configure the tunnel between a Cisco and Cisco and a Cisco and Thomson/Speedtouch ( apologies for calling the router a Speedtouch one minute and then Thomson the next).